Many time many of us have faced this problem that on double clicking the drives they don't open instead it will ask to "open with" ..
its happening because your system is affected with some virus which has created autorun.inf file in your drives.
Steps
1)Open the task manager and see the process tab and try to identify the unknown process and click on end task after selecting it
or process explorer from microsoft might help u
2)Delete its entry from startup too..
[registry startup also]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
3)start>run>then type cmd and press enter
type the following commands
4)C:\Documents and Settings\a>cd\ press enter
5)C:\attrib -s -h -r autorun.inf
6)C:\del autorun.inf
7)C:\D: (repeat these commands for each drive you have)
Friday, April 10, 2009
Driveguard.exe virus
driveguard.exe virus
Removal of Driveguard.exe virus is very easy.
1)Open taskmanager and end the process driveguard.exe
2)Any .tmp extension is running then also end that process.
3)type->run->msconfig -> remove its entry
4)Del from temp files.
Removal of Driveguard.exe virus is very easy.
1)Open taskmanager and end the process driveguard.exe
2)Any .tmp extension is running then also end that process.
3)type->run->msconfig -> remove its entry
4)Del from temp files.
Tuesday, April 7, 2009
Formatting a pendrive from Fat to NTFS
Plug in your pen drive. Click start & Right click on My Computer.
Select Properties > Hardware > Device Manager.
Expand Disk Drives & Click on your Pen Drive Name. ( In my case it’s : Jetflash )
Now Right click on your pen drive name & select Properties.
Go to Polocies Tab & Select Optimize for Performance.
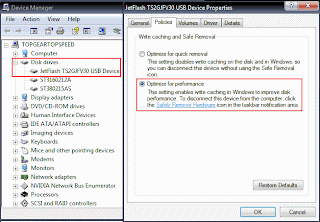
Click OK. Close device Manager.
Now open My Computer & Select Your Pen Drive ( ie Removable Disk ).
Right click on it & select Format. Click on File system box.
& Voila! You see the NTFS option.
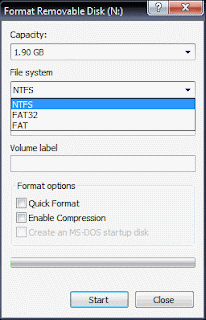
Now select NTFS & fromat your pen drive.
Select Properties > Hardware > Device Manager.
Expand Disk Drives & Click on your Pen Drive Name. ( In my case it’s : Jetflash )
Now Right click on your pen drive name & select Properties.
Go to Polocies Tab & Select Optimize for Performance.

Click OK. Close device Manager.
Now open My Computer & Select Your Pen Drive ( ie Removable Disk ).
Right click on it & select Format. Click on File system box.
& Voila! You see the NTFS option.

Now select NTFS & fromat your pen drive.

Sunday, April 5, 2009
Traffic generators
1)D-ITG http://www.grid.unina.it/software/ITG/download.php
2)pacgen - Ethernet IP TCP/UDP packet generating tool for Linux
http://nixbit.com/cat/system/networking/pacgen/
3)Hping is a command-line oriented TCP/IP packet assembler/analyzer download
4)Nessus Vulnerability Scanner from Tenable Network Security download
5)Tcpreplay is to resend all packets from its input file(s) at the speed at which they were recorded, at some specified data rate download
6)Nemesis is a command-line network packet crafting and injection utility for for testing Network Intrusion System download
7)PackETH is a *graphical* packet generator tool for ethernet download
2)pacgen - Ethernet IP TCP/UDP packet generating tool for Linux
http://nixbit.com/cat/system/networking/pacgen/
3)Hping is a command-line oriented TCP/IP packet assembler/analyzer download
4)Nessus Vulnerability Scanner from Tenable Network Security download
5)Tcpreplay is to resend all packets from its input file(s) at the speed at which they were recorded, at some specified data rate download
6)Nemesis is a command-line network packet crafting and injection utility for for testing Network Intrusion System download
7)PackETH is a *graphical* packet generator tool for ethernet download
Network Monitor Analyzer
1)Wireshark Network Protocol Analyzer-Network protocol analyzer for Windows and Unix that allows examination of data from a live network, or from a capture file on disk
download
2)Ethereal- A Network Protocol Analyzer
download
3)EtherApe is a graphical network monitor for Unix modeled after etherman.Featuring link layer, ip and TCP modes, it displays network activity graphically download
4)SNORT-SNORT is an Open Source Intrusion Detection System download
5)Argus-designed to monitor servers and network connections download
6)ngrep is a "network grep" utility that can be used to match regular expressions within network packet payloads download
7)Nagios for network and service monitoring download
8)NetworkActiv to sniff webpages on a Wi-Fi network download
download
2)Ethereal- A Network Protocol Analyzer
download
3)EtherApe is a graphical network monitor for Unix modeled after etherman.Featuring link layer, ip and TCP modes, it displays network activity graphically download
4)SNORT-SNORT is an Open Source Intrusion Detection System download
5)Argus-designed to monitor servers and network connections download
6)ngrep is a "network grep" utility that can be used to match regular expressions within network packet payloads download
7)Nagios for network and service monitoring download
8)NetworkActiv to sniff webpages on a Wi-Fi network download
Saturday, April 4, 2009
Password Cracker
1)Cain and Abel : The top password recovery tool for Windows
UNIX users often smugly assert that the best free security tools support their platform first, and Windows ports are often an afterthought.
download
2)John the Ripper is a fast password cracker, currently available for many flavors of Unix download
3)THC Hydra : A Fast network authentication cracker which support many different services download
4)L0phtcrack : Windows password auditing and recovery application
download
5)Airsnort : 802.11 WEP Encryption Cracking Tool download
download
6)Aircrack : The fastest available WEP/WPA cracking tool
download
7)Brutus : A network brute-force authentication cracker
download
8)Pwdump : A window password recovery tool
download
9)RainbowCrack : An Innovative Password Hash Cracker
download
UNIX users often smugly assert that the best free security tools support their platform first, and Windows ports are often an afterthought.
download
2)John the Ripper is a fast password cracker, currently available for many flavors of Unix download
3)THC Hydra : A Fast network authentication cracker which support many different services download
4)L0phtcrack : Windows password auditing and recovery application
download
5)Airsnort : 802.11 WEP Encryption Cracking Tool download
download
6)Aircrack : The fastest available WEP/WPA cracking tool
download
7)Brutus : A network brute-force authentication cracker
download
8)Pwdump : A window password recovery tool
download
9)RainbowCrack : An Innovative Password Hash Cracker
download
Rootkit detection
1)chkrootkit: checks locally on a host for signs of rootkits
http://www.chkrootkit.org/download/
2)RootkitRevealer: a rootkit detection utility
http://technet.microsoft.com/hi-in/sysinternals/bb897445(en-us).aspx
3)Ice sword: http://www.antirootkit.com/software/IceSword.htm
4)Rootkit Hunter: one of the newer rootkit checking projects
http://www.rootkit.nl/projects/rootkit_hunter.html
http://www.chkrootkit.org/download/
2)RootkitRevealer: a rootkit detection utility
http://technet.microsoft.com/hi-in/sysinternals/bb897445(en-us).aspx
3)Ice sword: http://www.antirootkit.com/software/IceSword.htm
4)Rootkit Hunter: one of the newer rootkit checking projects
http://www.rootkit.nl/projects/rootkit_hunter.html
Wednesday, April 1, 2009
How to disable Autoplay
Autoplay is also known as Autorun which should already be disabled for your cd-rom drives because of companies like Sony who like to install DRM on your computer without even asking you. There is a good article from Engadget on how to disable Autorun using a .reg file. This only works for CD-ROM drives and does not disable Autorun for USB drives.
There has been recent news of people gaining access to machines on an internal network using social engineering and USB drives. This guide will show you how to make sure that Autoplay/Autorun is disabled for all devices on your computer. It is highly recommended that you make sure Autorun is disabled for any computers you have access to at work that are running Windows XP. Disabling just the CDROM for your home computers is probably good enough since physical access to those computers is more restricted.
1. Click Start > Run
2. Type “gpedit.msc”
3. Computer Configuration > Click “Administrative Templates” > Click “System” > Double-Click “Turn off Autoplay”
4. Setting tab > Check “Enabled” > Select “All drives” from the drop down menu > Apply > Ok
disable-autoplay
There 4 easy steps to making sure that Autoplay (Autorun) is disabled on all your drives including the USB. That would remove the ability of people to insert a USB drive and automatically run a .exe on your computer by using a *.inf file.
The last thing that you can do to protect yourself is to make sure that you have “Hide extensions for known file types”. This will help you from accidentally clicking on a file that is on a USB drive that looks like it is safe to look at, but is not really. This is one aspect of social engineering that is dependent on the user to make the right decision.
Many criminals will try to mask the presence of a malicious file by adding on .exe to the end of a common file type. For instance .doc.exe or .xls.exe or .jpg.exe would be some examples. The file that you click on is not what you expect it to be rather a virus or a program used to compromise your system. Most anti-virus programs will catch this file after you execute it, but to be on the safe side it is best not to click on it in the first place.
- Open a local folder in Windows Explorer (not IE) like My Documents > Click Tools > Click Folder Options > Click “View” Tab > Uncheck “Hide extensions for known file types”
hide-extensions
Update
I updated some of the links that didn’t work, like the link to the news article about the Sony DRM and the old .reg file. I found a copy of the reg file somewhere else on the internet and rehosted it here so it doesn’t disappear again.
There has been recent news of people gaining access to machines on an internal network using social engineering and USB drives. This guide will show you how to make sure that Autoplay/Autorun is disabled for all devices on your computer. It is highly recommended that you make sure Autorun is disabled for any computers you have access to at work that are running Windows XP. Disabling just the CDROM for your home computers is probably good enough since physical access to those computers is more restricted.
1. Click Start > Run
2. Type “gpedit.msc”
3. Computer Configuration > Click “Administrative Templates” > Click “System” > Double-Click “Turn off Autoplay”
4. Setting tab > Check “Enabled” > Select “All drives” from the drop down menu > Apply > Ok
disable-autoplay
There 4 easy steps to making sure that Autoplay (Autorun) is disabled on all your drives including the USB. That would remove the ability of people to insert a USB drive and automatically run a .exe on your computer by using a *.inf file.
The last thing that you can do to protect yourself is to make sure that you have “Hide extensions for known file types”. This will help you from accidentally clicking on a file that is on a USB drive that looks like it is safe to look at, but is not really. This is one aspect of social engineering that is dependent on the user to make the right decision.
Many criminals will try to mask the presence of a malicious file by adding on .exe to the end of a common file type. For instance .doc.exe or .xls.exe or .jpg.exe would be some examples. The file that you click on is not what you expect it to be rather a virus or a program used to compromise your system. Most anti-virus programs will catch this file after you execute it, but to be on the safe side it is best not to click on it in the first place.
- Open a local folder in Windows Explorer (not IE) like My Documents > Click Tools > Click Folder Options > Click “View” Tab > Uncheck “Hide extensions for known file types”
hide-extensions
Update
I updated some of the links that didn’t work, like the link to the news article about the Sony DRM and the old .reg file. I found a copy of the reg file somewhere else on the internet and rehosted it here so it doesn’t disappear again.
Subscribe to:
Posts (Atom)